Security CheckUp: Simplifying risk review in M365
Lire l'article[NEW] MYDATAMANAGEMENT TO CLEAN UP YOUR OBSOLETE, UNUSED AND VOLUMINOUS DATA
Solutions
Effective response to six major challenges in data security
#1 user-interacting platform for detection
Discover the platform
Best practices to improve Microsoft Teams security
Download the infographicOur resources
Check out our useful resources for improving data protection
Microsoft 365
08 December 2021

In a context of crisis and widespread remote working; The use of collaborative tools such as Teams was essential to maintain the fluidity of remote exchanges between employees.
The total control of the functioning, the sharing, configurations that the tool offers is a particularly sensitive subject, especially for Microsoft 365 data protection.
Microsoft Teams application has seen a surge in usage since March 2020. It is growing from 44 million users to 145 million in less than a year. (1)
Teams holds a powerful feature set that has been growing steadily since its inception in 2017 (instant messaging and calling, video conferencing, task scheduling, project management, and file sharing and storage) . With this collaborative tool, users have a great autonomy of use. This is what makes it a complex tool, both to manage from an administrative point of view but also for the users who are confused in their uses.
According to an IFOP survey, 25% of employees don’t use some IT tools (shared documents, remote connection, collaborative tools, etc.) for fear of security or confidentiality problems.
The autonomy of users, the collaborative nature of the tool and the emergence of new functionalities pose real constraints for IT teams. Indeed, They are faced with a large volume of data to supervise. They must adapt their security policy so as not to block too much or give too many rights to users in order to reduce risks. And let’s not forget that the massive adoption of Teams was recently done in a context of crisis and emergency. Plus, the cyber context puts additional pressure in the detection of intrusions and threats.
So how do you ensure better data governance and protection for Microsoft Teams ?
With Teams, employees have become hyperconnected thanks to its application that acts as a personal messaging application (Messenger, WhatsApp…). Exchanges between teams have become very accessible: from anywhere (at home, on vacation or at the office), from any device (e.g. tablet, mobile, laptop) or at any time. This ultra-connectivity creates risks for the company’s data and requires IT teams to be even more vigilant. Who does what ? And can do what ? Who shares what ? Data sharing evolves instantaneously and can give way to malicious intent or compromission (e.g. identity theft, access from a suspicious country or connection from a new device).
Each user can be a member of more than 1000 different Teams. (Microsoft)
A Teams team may include 25000 members (Microsoft)
Teams and SharePoint are two tools that complement each other.
Teams files are stored in SharePoint:
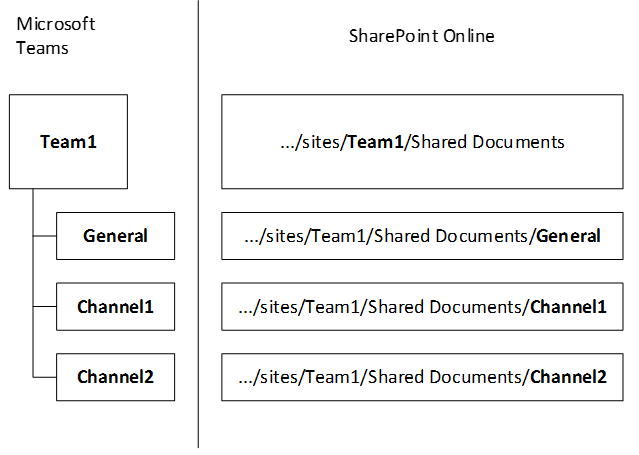
Each time a Teams « crew » is created, at the same time SharePoint will create a file library to manage and store the documents of the space (e.g., “files” tab in Teams). The SharePoint library is directly accessible through the Teams channel.
SharePoint backs up files deleted from Teams: it is not possible to recover a deleted file via Teams but via the SharePoint trash associated with the Team for a duration of 30 days.
Teams has three levels of access:
It is possible to refine these access rights via SharePoint online.
The risk of fraud on Information System through access, configuration or sharing can be significant for a company. The risks and threats are numerous.
MALICIOUS/ ILLEGITIMATE SHARING: Data shared with one or more correspondents can be disclosed against the user’s will if one of the accounts is compromised. The occurrence of the risk can be complex to detect as it requires the user to be aware of it.
ANONYMOUS / ILLEGITIMATE SHARING: The increase of sharing methods means that a configuration error is always possible. This error can come from the user or the administrator. (Ex: A collaborator shares a sensitive file via an anonymous link to a colleague. If the latter decides to transmit the link to another person or to an external account, an information leak can quickly occur…)
EXTERNAL / OUTDADED SHARING: It is important to have control over your rights so that they don’t become obsolete at a given moment. To do this, it is important to check if the people who have access to the data are still legitimate to access it (e.g.: service provider on an old project).
In order to avoid human errors and risks of data leakage, it is important to permanently control accesses, rights, shares and configurations on Teams.
Ensure that data at any given moment in time is accessed and shared by and with the right people. Inside and outside the company:
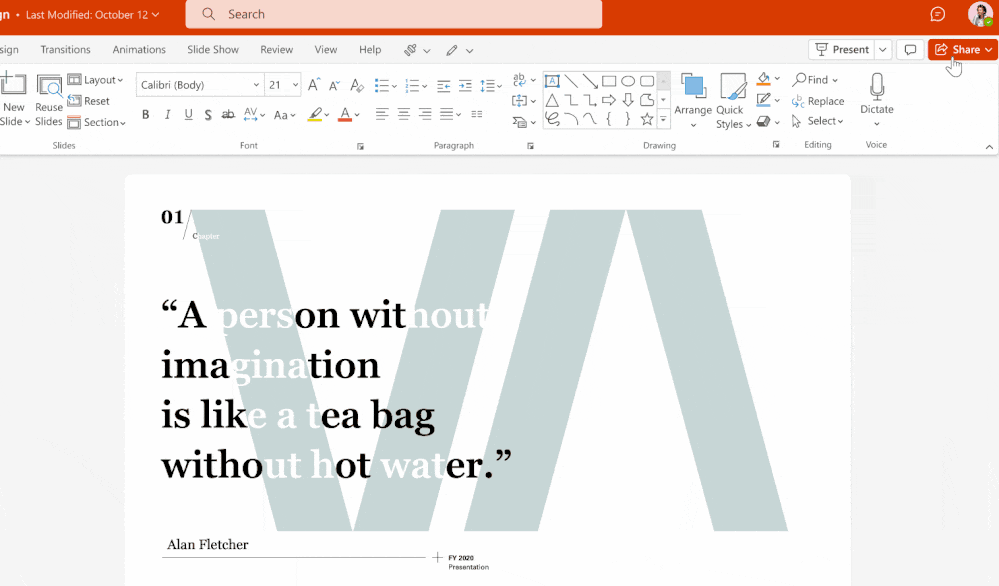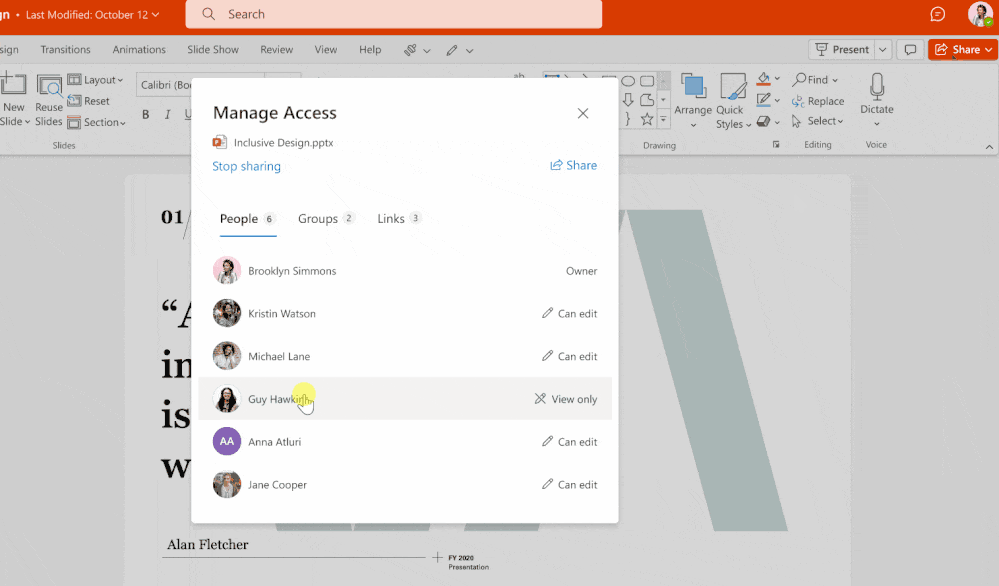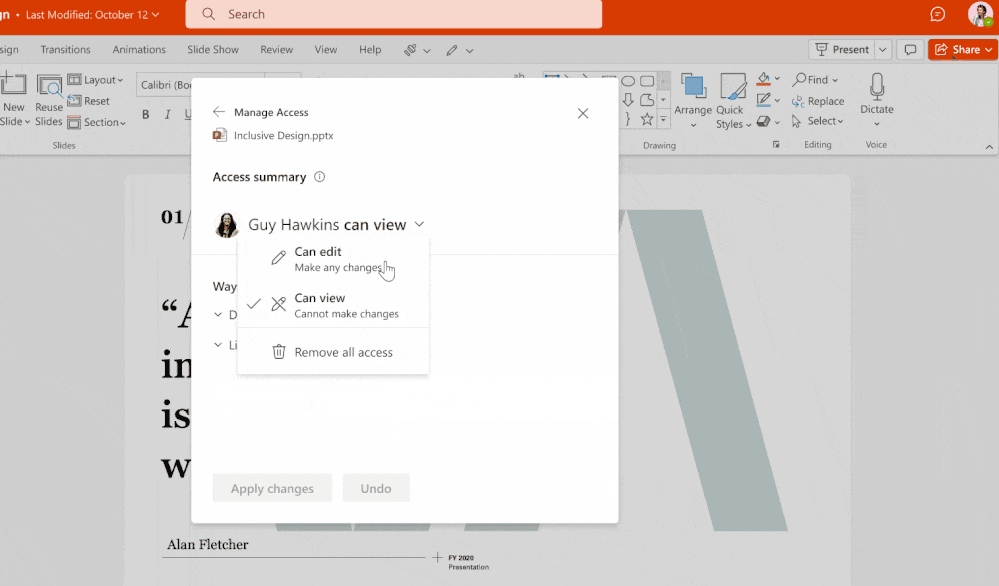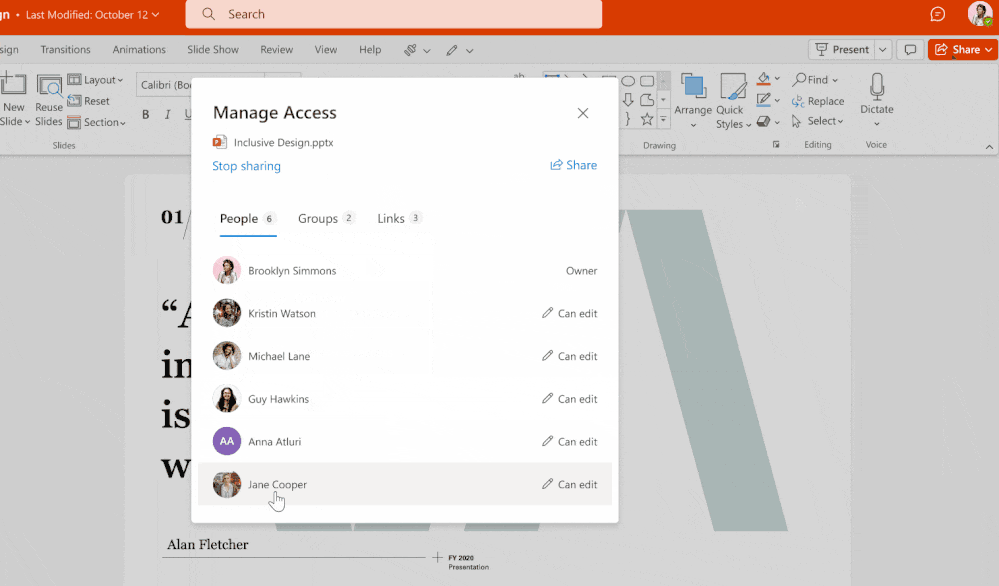
Concerning sensitive data, it is important to identify and map them: where are they located? which people have legitimate access to them? who can access them? in order to define the levers to be put in place:
As a reminder, it is possible to apply rights and sharing restrictions on a specific folder or directory via SharePoint online.
It is important to control the sharing in Teams to avoid malicious, illegitimate or anonymous sharing.
• Do not give too high rights to some members : Establish a scale of rights according to the member, in order to avoid human errors. (e.g. the principle of least privilege which allows to restrict the access rights of a specific user, so that he has access only to the files necessary to perform his work).
• Avoid rights escalation: Each member having received rights on a file. Then they can share it with other non-legitimate members. It is therefore important to define who should be given the rights to confidential data.
“60% of cyber-attacks can be attributed to inappropriate human behavior” – Accenture
It is important for IT and Digital Workplace managers to raise awareness and involve employees in the dangers of data leakage. Employees must become more familiar with the tool to avoid any handling errors.
To raise cyber awareness among employees, companies can implement various actions:
- Workshops: This format of meeting allows to work in a collaborative way with the collaborators. In order to sensitize them to the use of collaborative tools like the creation of Teams or functional channels on Teams.
- Training: The purpose of training employees is to make them aware of several functionalities of the tools. The possible uses to be transcribed in their daily life and in the uses of their company. (e.g., in the context of remote work where the use of Teams has been very important)
- Recertification campaigns: Setting up campaigns with employees allows to remind them, at the desired frequency, to maintain the correct rights on Teams and to identify any configuration error.
- Internal communication: Companies can implement various marketing actions such as emailing to remind the issues of data protection. (in the use of Teams, SharePoint or OneDrive).
These various awareness-raising actions will also allow them to become more involved in the protection of their data, and to make them more responsible by:
→ A better use of their collaborative tools
→ Autonomous management of their access, rights and sharing
→ An up-to-date review of rights over time
Giving users visibility into the use of their data reassures them, involves them and encourages them to use the tools wisely.
According to a recent IFOP study, more than 8 out of 10 employees want to be involved in the security of their company’s data. (IFOP). And 81% of the employees surveyed would like to have a dashboard to track who is doing what? Who can do what? Who has access to what?
Indeed, a better visibility of users on their accesses, rights, sharing has several benefits:
Awareness and visibility allow users to gain efficiency in the use of Teams, SharePoint and OneDrive and to avoid heavy consequences of a configuration error related to the normal activity of a user.
On Teams, owners must also have a perfect vision of the composition of their Teams and channels to quickly correct configuration errors:
Doing so via a simple and user-friendly tool would allow the user to be more involved in the sound management of his data, and that of the company, as well as in the appropriation of the various risks of data leakage.
Collaboration and cybersecurity are the two main challenges of data protection for companies. Involving users seems to be a must today, given their autonomy in the use of collaborative tools, and the constant evolution of an increasingly powerful tool like Teams.
IDECSI solution “MyDataSecurity» allows each employee to have maximum visibility thanks to a personalized dashboard grouping rights, accesses and shares. The user can identify at a glance its configuration errors and anomalous behaviors and then report them to the IT teams or remedy them directly. And thanks to an expert back office, IT teams can supervise operations and gain in efficiency (SOC optimization, analysis). IDECSI relies on preconfigured threat models and real-time alerting of the most virulent threats.
With IDECSI, you benefit from a SaaS platform for monitoring, detection, auditing and remediation of Microsoft 365 and on-premise data, and position each user as a contributor to the security of their company.
1. Microsoft Teams compte désormais 145 millions d’utilisateurs actifs quotidiens (siecledigital.fr)Recent articles
Subscribe to our newsletter and receive new contents every month
Our articles
These articles may
interest you