[Conference] How to master Data Access and Sharing in Microsoft 365
Lire l'article[NEW] MYDATAMANAGEMENT TO CLEAN UP YOUR OBSOLETE, UNUSED AND VOLUMINOUS DATA
Solutions
Effective response to six major challenges in data security
#1 user-interacting platform for detection
Discover the platform
Best practices to improve Microsoft Teams security
Download the infographicOur resources
Check out our useful resources for improving data protection
Idecsi News
04 December 2017
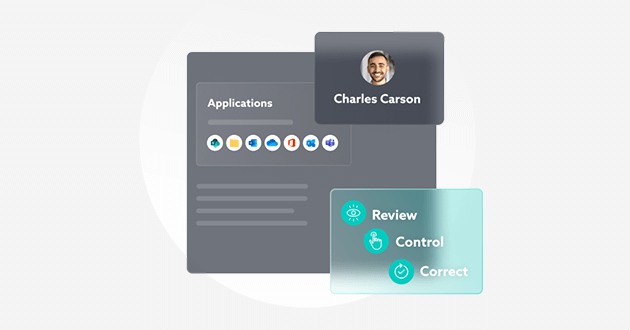
Companies need efficient and cost-effective methods to detect targeted email attacks launched via a compromised account or identify those using brute force methods to steal corporate Microsoft Office 365 login credentials.
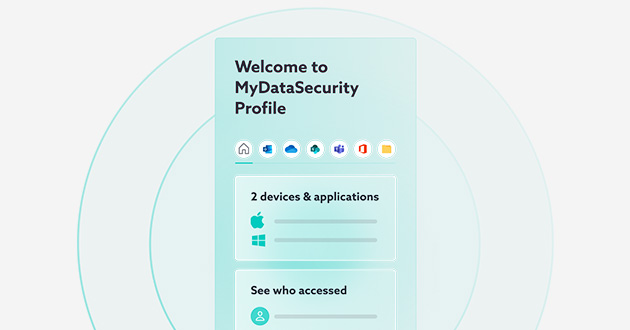
With the IDECSI MyDataSecurity, every user has the means to monitor their security, identify and report fraud, illegitimate access, or malicious settings immediately. Defence becomes collective, security is increased and processing time and costs are optimised. We asked our cyber security expert to share his view on what makes an ideal solution based on customer experience and feedback.
Security investment is migrating from Identify and Protect to Detect and Respond (and Recover if you prefer the NIST formulation)1. In this migration, we have been showered with highly sophisticated SIEM, IDS and UEBA solutions – many of which apply advanced mathematical techniques, artificial intelligence and machine learning, to identify suspicious patterns in our networks.
One challenge with these solutions is that they require significant investment, not just financially, but in expert resources that must be dedicated to driving these platforms. One CISO grumbled to me that they had inherited one of the most sophisticated IDS platforms, but it was like a Ferrari in the basement, in home where nobody had a driving licence.
Don’t get me wrong, the solutions are exceptional in the things they can identify. The protection and safety they deliver is a must-have for any substantial company, and if you can afford it, smaller organisations too.
That said, I’d like to explain how we need to evolve our detection approach in an evolving IT landscape. The answer is MyDataSecurity. A solution which requires minimal resources to deploy, minimal resources to run, significantly expands detection capabilities, and engages users in their cyber protection.
IT is a driver of organisational growth and a key focus for executives(2). But it also drives new detection challenges – primarily around user access. More applications, more users accessing corporate data, more data shared in more ways, more methods of access. All of these drive some critical questions:
So what’s this got to do with security ROI? If you want to secure those applications, by detecting breaches in real time, you might think that your SIEM, IDS or UEBA is the right starting point. But simply pushing the relevant logs into those platforms will be astonishingly expensive – one customer told us the license cost for submitting only Exchange logs to their seam would be €1.2m.
Gartner tells us that “to do monitoring right, solutions often require a significant increase of staff, including very high-priced threat investigators”3, and, in the case of the questions above, these expensive investigators ultimately have to call the user and say “was this you?”. Not efficient.
Which brings us to the solution, MyDataSecurity. For more information on what exactly I mean by the MyDataSecurity, take a look at this post. But in summary, it understands the applications it’s protecting, it profiles every single user and every single library and every single resource which it is protecting, and it communicates in user language directly with the user, giving them straightforward remediation responses.
The ROI is tremendous. To quote one of our customers “95% of the alerts can be managed by the end user”. MyDataSecurity technology can be deployed extraordinarily quickly and easily – it doesn’t need intrusive access to applications or network, it doesn’t need to see the confidential data it’s protecting, it doesn’t need to learn how each application works (it’s application aware, remember). To go from zero to full protection can happen in three months, with the resource investment measured in hours, perhaps days, but certainly not weeks, months or years.
Ben Miller is an experienced technologist and entrepreneur with a background in mathematics and software engineering. He is focused on bringing new technologies to market, which change conventional thinking. Within cyber security, we have long been used to complaining about users, and driving more work into the security team. Ben’s particular focus today is technologies which challenge this approach and instead make user empowerment a key part of the cyber discussion.
[1] Gartner: Shift Cybersecurity Investment to Detection and Response
Recent articles
Subscribe to our newsletter and receive new contents every month
Our articles
These articles may
interest you

[NEW] DETOX to get rid of M365 risky sharing and data access
Lire l'article