Security CheckUp: Simplifying risk review in M365
Lire l'article[NEW] MYDATAMANAGEMENT TO CLEAN UP YOUR OBSOLETE, UNUSED AND VOLUMINOUS DATA
Solutions
Effective response to six major challenges in data security
#1 user-interacting platform for detection
Discover the platform
Best practices to improve Microsoft Teams security
Download the infographicOur resources
Check out our useful resources for improving data protection
Security
10 October 2018
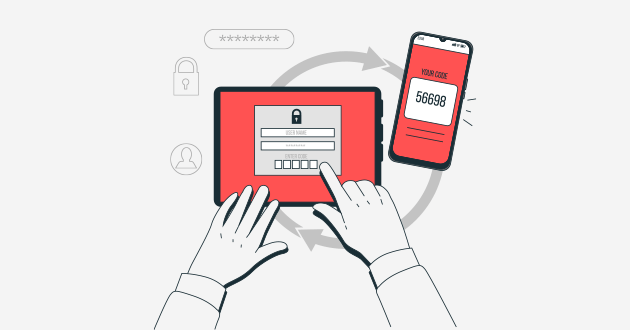
I wrote in a recent blog that multi-factor authentication (MFA) is not a panacea to ensure security of your accounts. It’s a useful tool – although many customers complain about the manageability and usability of such solutions – but more and more, MFA is being defeated. On the one hand, that’s just business as usual – ‘twas ever thus in the security arms race, since the first lock-and-key was invented 6000 years ago. On the other hand, MFA deployments give both users and security teams a sense of security which is increasingly false.
MFA solutions rely on a simple principle: after demanding username & password, they ask for an additional piece of information which, typically, cannot be compromised quite as easily as your standard credentials. A code sent to your mobile is most common today, memorable words from which you only enter a few characters are popular, separate physical devices are used by many banks. But they all suffer from the same shortcoming: once you’re challenged for the second factor, you enter it into the same interface, typically a web front end, in order to access the service you are logging into.
So to compromise your MFA, all I have to do is to hijack the communications between you and the service. Once I do this, the service will challenge you for your second factor, and you will merrily input it, feeling quite safe, while you’re actually going through my intermediary, allowing me straight into your email, or whatever it is you’re accessing, right alongside you.
And it turns out, it ain’t that hard to hijack that communications channel. There are two common options today:
Would your users fall for a malicious WiFi? My guess is yes. How careful are even sophisticated users regards what network they log onto? If you see Starbucks_WiFi_1 in the coffee shop, do you think twice, or do you just assume it’s okay? Even if you are super careful, are your users? In one recent attack ‘a fake wireless access point had been operating near [an] event which intercepted requests’1. And it’s so incredibly simple to do – all you need is a router and a 4G connection. No targeting, just wait to see what you get.
A malicious splash page is also pretty straightforward. Our friends at Bing have made it surprisingly convenient for bad guys to buy an ad word which allows a false splash page to leap to the top of the rankings2 (to be fair, they are quick to take it down when they are notified, but that still leaves plenty of time to catch some unfortunate punters).
However, it’s phishing that really excels here. Dodgy emails, dodgy adverts and dodgy websites all push you to apparently legitimate splash pages. Switched‑on users may check the URL, but with more sophisticated attacks, that’s impossible. Never mind that lowercase L and uppercase I are typically identical, the use of punycode3 allows attackers to encode URLs that look completely legitimate, but actually have Cyrillic (or other characters) encoded in Roman looking characters.
Amnesty International (yes the human rights folks) recently published research, showing exactly how this type of false splash page is used to compromise MFA, along with the phishing that leads you there3. Although, if you’ve been paying attention so far, it’s going to tell you more-or-less exactly what I just wrote.
So what next? Well, if you’ve been reading this blog, or anything else from IDECSI, over the past few months, you’ll know our view is that the key is monitoring and detection. You can put in place as many preventative mechanisms as you like, and don’t let me stop you deploying MFA, it does make it harder for hackers, but monitoring and detection is critical.
By understanding normal user behaviour, on a per user per application basis, we can identify when the bad guy gets in. Moreover, our Personal Security Guardian is designed to engage your users in this process – massively reducing the time to breach identification, minimising the cost of the breach, and significantly improving your users’ cyber awareness.
Ben Miller is an experienced technologist and entrepreneur with a background in mathematics and software engineering. He is focused on bringing new technologies to market, which change conventional thinking. Within cyber security, we have long been used to complaining about users, and driving more work into the security team. Ben’s particular focus today is technologies which challenge this approach and instead make user empowerment a key part of the cyber discussion.
[1] https://www.mwrinfosecurity.com/assets/Whitepapers/Case-Study-Phishing-for-Credentials.pdf
[2] https://hotforsecurity.bitdefender.com/blog/search-for-chrome-on-bing-and-you-might-get-a-nasty-surprise-20501.html
[3] https://tools.ietf.org/html/rfc3492
[4] https://www.amnesty.org/en/latest/research/2018/12/when-best-practice-is-not-good-enough
Recent articles
Subscribe to our newsletter and receive new contents every month
Our articles
These articles may
interest you

OneDrive Security: Three Points of Attention to Better Control Your Data
Lire l'article