Security CheckUp: Simplifying risk review in M365
Lire l'article[NEW] MYDATAMANAGEMENT TO CLEAN UP YOUR OBSOLETE, UNUSED AND VOLUMINOUS DATA
Solutions
Effective response to six major challenges in data security
#1 user-interacting platform for detection
Discover the platform
Best practices to improve Microsoft Teams security
Download the infographicOur resources
Check out our useful resources for improving data protection
Security
17 June 2022

The access and authorizations review, or re-certification, consists of ensuring that the access of users to data comply with the Microsoft 365 security policy of a company and institutions (both public and private) and with the user’s activity.
Often implemented and mastered in on-premises and internal company environments, the principles of access review seem much more complex to implement today in the cloud, especially since the users have become administrators in their accounts.
Why is it necessary to improve the recertification process? How to effectively engage employees in the access review process?
Access review consists of revalidating access and permissions at a given moment and identifying risks related to access, rights and file sharing, in order to maintain sound data governance in terms of security and compliance by reducing the vulnerabilities of the information system.
But with the digital transformation and the accelerated use of collaboration tools by employees, the access review has evolved and its functions have expanded to cover better risk management.
The access review is part of a strategic cybersecurity plan for a company, and helps to manage the risk inherent in the control of information sharing, particularly on Microsoft 365 collaboration tools.
Poor command of collaboration tools can lead to unintentional incidents of data leaks by employees. Indeed, log analysis is far too important to be able to track and secure each and every access, right, sharing and configuration at the global enterprise level.
The access review process can no longer be limited to having employees validate access and rights to an email or storage space. It must now determine the owners of lists, folders, files, accesses made, inherited rights, sharing configurations (anonymous, company link), synchronized devices, applications with rights on the data (SharePoint, Teams, OneDrive).
With the digital transformation, many regulations and standards have emerged in recent years to frame and regulate this issue, such as the GDPR law.
Companies have to comply with a range of obligations and applicable laws regarding their data, which vary in stringency depending on the sector of activity (e.g. banking and health sector). They are subject to auditing obligations to check the extent to which national or even European directives are complied with by the company.
It is necessary to prove that the confidentiality and integrity of the data are respected, that access to sensitive files is legitimate and that the data are accessed by the right people.
In this context, access review will make it possible to rectify and correct, if necessary, access, rights and sharing, and to legally protect the integrity of data (e.g. communication channels in Teams, data exchanged internally and externally).
Having a compliant security policy allows you to hold recognized standards such as ISO 270001 certification. It aims to protect the company from data loss and corruption and provides a conceptual best practice for overall security.
Access review will also serve ecological interests by allowing the user to have better digital hygiene and to be part of a Green IT approach by making an inventory of files to be deleted or no longer used on their email or OneDrive.
Data protection has become a real strategic issue for companies as it can have economic, legal and judicial impacts. However, access review cannot be done without the user, and engaging the user in this process can meet many awareness, adoption and remediation objectives.
One of the key principles of the access review is the accountability of the reviewers. Today, who better than the users to revalidate and correct the access and rights on their own files, of which they are now the manager?
Users have almost become administrators for the access and sharing of their files. They should be able to follow what is happening with regard to their data and remove access as easily as they share it.
To do this, it is important to give them intuitive and easy-to-use tools. By having better visibility of their operations, users can more easily become active and responsible in protecting their data.
Including them in the access review process will allow them to become actors in the life cycle of what they share, the legitimacy of access permissions given, and the configurations set up.
In addition to maintaining better digital hygiene, the review of autorizations will increase employee confidence in the collaborative tools Teams, SharePoint and OneDrive. This helps to raise awareness particularly of good security practices for collaborative tools.
The access review is a large and complex project for IT teams to implement due to:
The key factors of a good access review are the automation of tasks, the visibility of operations performed and the identification of file and group owners. These factors allow good control over time of access, rights and sharing for the security and compliance of data.
User involvement in the access review process is nowadays unavoidable in view of the context. However, the process can sometimes be complex to implement when a large volume of data needs to be analyzed in a short time. To meet these objectives effectively, it is possible to use an expert solution to manage this volume and gain in analysis and remediation capacity.
IDECSI has developed a unique solution to simplify the access review in 6 major steps and to effectively involve the employee in the security system.
Thanks to an interactive, user-friendly and personalized IDECSI dashboard: MyDataSecurity, employees have a unified view of the operations carried out on their data (e.g. rights, access, sharing). It can perform a quick scan of its environment during an entitlement review process. He receives notifications from the IT teams in order to validate or not certain operations. If they notice an anomaly, they can remedy this directly by themselves, and have the possibility to alert the IT teams if compromises become apparent (e.g. rights that they did not create themselves).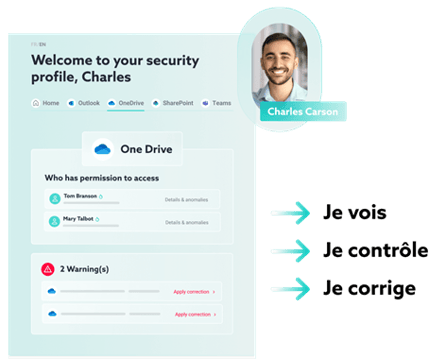
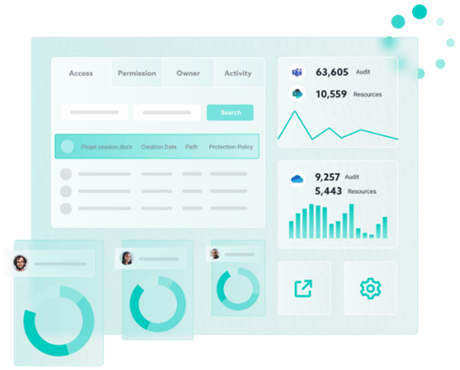
At the same time, IT teams also have a centralized view of the operations performed by users thanks to Advanced Monitoring.
This allows them to more easily feed back information to the user and automate security operations. The implementation of an access review is then simplified by the involvement of the user and a centralized visibility of operations allowing:
The autonomy of employees in the use of collaborative tools has encouraged human and configuration errors. However, they are in the best position to know whether their permissions are legitimate.
It is therefore important to integrate them into the access review processes for better governance of data over time from a security and compliance perspective.
To simplify this access review , it’s important to have an expert solution that can give IT teams and employees visibility into the permissions granted on Teams, OneDrive and SharePoint. IDECSI’s unique solution allows a collaborative and multiplied detection, through user involvement, automated mechanics and fine analysis of your data.
Recent articles
Subscribe to our newsletter and receive new contents every month
Our articles
These articles may
interest you

OneDrive Security: Three Points of Attention to Better Control Your Data
Lire l'article