Security CheckUp: Simplifying risk review in M365
Lire l'article[NEW] MYDATAMANAGEMENT TO CLEAN UP YOUR OBSOLETE, UNUSED AND VOLUMINOUS DATA
Solutions
Effective response to six major challenges in data security
#1 user-interacting platform for detection
Discover the platform
Best practices to improve Microsoft Teams security
Download the infographicOur resources
Check out our useful resources for improving data protection
Microsoft 365
17 April 2020
Now that home office has become the constrained new standard for most companies, the use of virtual communication tools and collaborative applications drastically increased leading to an escalation of security incidents and cyberattacks. How to ensure that companies and even users stay in control during times of crisis?
Usually, companies have implement security protocols including threats and fraud detection systems when deploying in the Cloud. However, this unprecedented situation seems to challenge established processes in some ways: upsurge in the connection origins, malicious applications, access to sensitive data, unintended shares and suspicious non-secured files…
3 points that our experts recommend to closely monitor to secure Office 365:
Home office, the blur distinction between private and professional use of devices (PC, professional smartphone, tablet…) and the use of collaborative platforms lead to potential weaknesses for companies.
Applications that synchronize to the IS can have partial or full rights, malicious or suspicious behaviors. For instance, the videoconference application Zoom was recently suspected to leak personal data.
While users are becoming increasingly aware of phishing attempts through identity theft and password theft as a result of cybersecurity awareness training efforts, they are often not trained to deal with phishing cases through rights or App permissions.
Data leak from a user account is most of the time invisible to the user as it often comes from a disguised malicious application:
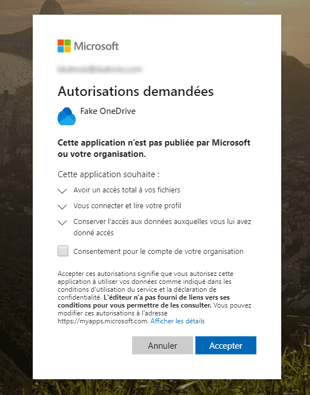
Remotely, users are less sensitive to the security of downloaded and used apps, and may not pay attention to the rights they grant to these applications. Awareness of this new type of fraud seems in this context crucial.
With home office, it should be of primary concern to be aware of how data are managed. Data transfer from on-premise to SharePoint or OneDrive directories that does not meet all security standards is made easier. Files will tend to wander around rather than stay in a secure SharePoint on-premise site.
In order to prevent data leaks, or Data Loss Prevention, here are some tips:
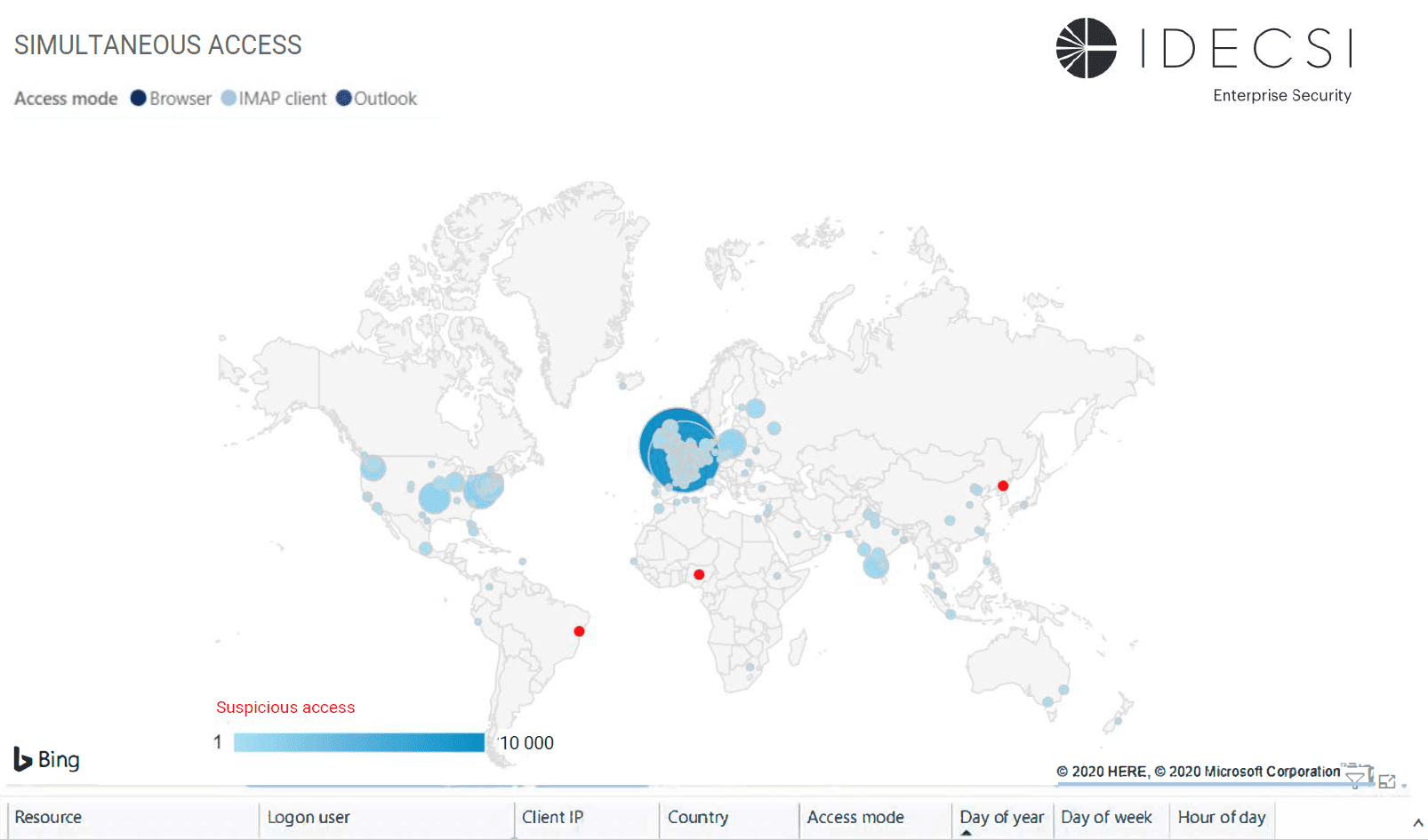
With everyone remotely accessing the company’s applications and the explosion of new IP addresses, it is important to pay special attention to connection origins. The detection systems set up so far are often based on a certain rule model and not necessarily adapted to extreme situation or times of crisis.
Therefore, it is important to try to identify origin anomalies through:
Moreover, monitoring the Office 365 environment will help to detect if there is a connection from a suspicious country, for example, by using the country predicate alert of the IDECSI monitoring platform.
Other use cases are preconfigured in our solution for efficient detection: Transport rules, Journal rules, Smtp Forward, Access mode (IMAP protocol), Full access to a mailbox, eDiscovery, VIP resource access or sharing (protected folder), Full Download, Unknown App permission...
Lastly, here are some key steps in case of Business Email Compromise or fraud attacks:
The IDECSI technology for monitoring O365 activity identifies any suspicious action: suspicious connection origin, fraudulent access, malicious configuration or external sharing.
The platform includes tracking, alerting, auditing and reporting on the collected data of an Office 365 tenant: usage, settings, data,... among the different applications: Exchange, SharePoint, OneDrive for Business, and Microsoft Teams.
Recent articles
Subscribe to our newsletter and receive new contents every month
Our articles
These articles may
interest you