Security CheckUp: Simplifying risk review in M365
Lire l'article[NEW] MYDATAMANAGEMENT TO CLEAN UP YOUR OBSOLETE, UNUSED AND VOLUMINOUS DATA
Solutions
Effective response to six major challenges in data security
#1 user-interacting platform for detection
Discover the platform
Best practices to improve Microsoft Teams security
Download the infographicOur resources
Check out our useful resources for improving data protection
Microsoft 365
08 December 2021

The health crisis has suddenly shaken up our working habits and has made companies across the world to rethink their digital transformation. This change has been made possible by massive and rapid deployments of tools such as the Microsoft 365 suite to help employees collaborate remotely. Our activities and the way we work have been transformed at a great speed.
According to a Gartner study, 1 in 5 employees say being an expert in the use of digital tools and half consider themselves to be competent. Employees have taken control of these tools and have developed new digital practices.
Despite an expressed digital maturity, vulnerabilities persist, particularly around shadow IT and human error. According to a CESIN study, negligence or handling errors by an internal administrator or an employee are one of the main causes of security incidents. A misuse of tools can compromise the security of their data in Microsoft solutions.
This is why, today, employee awareness of security issues is essential to work with these tools.
Discover some best practices to share with your teams to help them better protect their data from Microsoft 365 tools: OneDrive for Business, Microsoft Teams and SharePoint Online.
OneDrive is a cloud-based collaboration platform. Employees can store and back up documents. By storing the work files in the cloud, employees can access and edit their personal work wherever they are and from any device.
With OneDrive, they can also share their work documents with colleagues or external partners everywhere in the world.
With the implementation of the Microsoft 365 suite and particularly OneDrive, employee has less need to call on the IT department to share and configure rights and therefore gains autonomy. Security options can be activated to protect access to a OneDrive library, for example with code authentication or multi-factor authentication applications. As far as document sharing is concerned, the user is in control of the information and the sharing they wish to do. This part presents risks if the user is not careful. Raising awareness of good sharing practices, therefore, seems essential for good control of the tool.
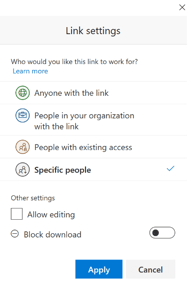
There are several options of sharing from OneDrive:
|
Anyone |
Give access to anyone who receives this link, whether they receive it directly from you or forwarded from someone else. This may include people outside of your organization. |
|
People in your organization |
Give anyone in your organization who has the link access to the file, whether they receive it directly from you or forwarded from someone else |
|
People with existing access |
Send a link to somebody who already has access |
|
Specific people |
Give access only to the people you specify, although other people may already have access. If people forward the sharing invitation, only people who already have access to the item will be able to use the link |
|
Allow editing |
People can edit or can only view files |
|
Open in review mode only |
Recipients open in edit mode to make tracked edits or leave comments |
|
Block download |
People cannot save a local copy |
It is important to raise awareness of the risks of open sharing. The options 'Anyone’ or 'People in your organization' can lead to unwanted access and modification. Indeed, when sharing, people are free to forward from someone else.
It is therefore important to always check the sharing settings and give the right permissions to the right people. It is preferable to use 'Specific people' sharing to limit sharing to authorized people.
If you share a document for consultation to an external person, it is also useful to disable the modification and perhaps even to block the download. The partner will then no longer be able to create a copy of the document on his computer or make any changes to it.
Another good security practice is to manage access rights to shared documents. With OneDrive, a sharing is not permanent. Owners can check rights at any time. As the owner of their space, employees are responsible for their data and sharing they make.
Each user can go to the 'Shared' section and the 'Shared with' tab in their OneDrive online. There they will find all the documents shared with other users. Thanks to this view, they will be able to detect if sharing are obsolete and therefore delete them.
This revalidation of rights on OneDrive is an important step to share with your colleagues to maintain a hygiene of rights and improve data protection.
Microsoft Teams is a collaboration hub for teams where all conversations, meetings, files and notes can be accessed by everyone, all in one place. It’s a place for collaboration, projects and communication.
Collaboration may deal with confidential matters, sharing of sensitive information and even with external partners. For all these reasons, it is important to understand the Microsoft Teams tool with its specificities and to respect some rules of good use to keep control of your professional data.
Teams offers the ability to send messages through chat or through work groups called 'Teams'.
Chat conversations are used for informal communication. Indeed, this communication channel does not allow to have a total guarantee on who can access the information. A chat cannot be deleted and any member of a conversation can add employees into it. There is no notion of an owner or guarantor of the information exchanged. Therefore, team or emails are recommended for sharing sensitive information or group collaboration.
When someone shares a document in a private Microsoft Teams chat, the documents are automatically stored in a document library in OneDrive. Rights and permissions are also automatically granted to all participants in the conversation according to the organization's configuration rules. A regular check helps to have control over access rights of previously shared documents.
As access management is not directly accessible in Teams, your collaborators may feel lost. It can be interesting to communicate on the relationships, OneDrive, Teams, SharePoint in order to help them find their information and facilitate a potential revalidation of sharing on their documents.
Teams is a way of bringing together work groups. The sharing of information is under control and more long term compared to private chat. Some good security practices are still important and must be implemented on these teams.
A good security practice with Teams is to always create private teams. Unlike a public team, a private team will have the advantage of better managing the team members. Only owners can add or remove members.
Moreover, when you add a member or an external guest to a Teams team, this person has access to the whole team, documents, conversations and added applications. So you have to be careful with the information you share and regularly check who can access it.
NB: It is now possible to be a member of a channel and not a member of the team thanks to shared channels. The member review will also have to be done on these specific channels.
A tip to communicate : an icon is visible in Teams indicating if there are any externals members. 
Before integrating a guest, the owner or the person in charge of the addition is responsible for checking if confidential data is not accessible in the team. When the guest has completed the team work, deletion of the member is recommended. A review of access and external guests can be initiated by the space managers according to the progress of the project, for example at the end of each stage, per month or per quarter.
It may also be suggested to always add two team owners to ensure that there is always an owner present to moderate information and team members.
If certain data or documents to be shared are sensitive and should not be accessible to all members, and in particular to external parties, you can create private channels within Teams.
Private channels will allow you to refine the audience within a team with publications, documents, applications only accessible to authorized persons. The information on these channels will then be more controlled.
If you want to make a document completely inaccessible, you have to delete it from the Trash. Indeed, when a document is deleted in the teams team, it remains in the Trash space of your associated SharePoint site. The user will then have to access the SharePoint site and delete the document also in the trash. The deletion will then be final and access will be impossible.
The Teams tool offers many possibilities for employees. Supporting them in the best way to share information is essential to encourage their adoption.
SharePoint is also a very powerful tool in the Microsoft 365 suite and can be used in different ways: as a communication site (intranet), as a storage site for finalized documents, as a team site (linked to Teams).
The multiplicity of uses and functionalities makes it a complex tool for the user and can be dangerous for the security of the company's information and data. We share some examples of simple best practices to apply to SharePoint for your employees.
Before starting to build a SharePoint site, the user should have a clear idea of what information they want to find.
In order to avoid having thousands of unused or misused sites, some IT teams may decide not to open the site creation to employees. In this case, they have to go through an administrator to qualify the request and help build the site.
If, you have left the choice to the employees, you will have to guide them in the creation.
It can be interesting to propose a workshop framework to help and optimize the creation of a SharePoint site. This will help the user to define a clear structure with the information, documents, lists and pages to be created.
Here is an example of a workshop outline, to define the elements to be found and therefore the structure:
Once the structure has been created, the navigation should be defined and the parts and sub-parts should be clearly named for all users of the site. By involving them in the creation, users will be more likely to collaborate and use the platform.
SharePoint allows you to define the permissions and rights for users. For example, you can give very specific access to a reduced number of people on a folder or document only. However, the risk is to get lost in the permissions you give.
It is interesting, especially if you are talking to a user who is new to SharePoint, to suggest that they use the standard groups: Owner, Members and Visitors and not to work directly on specific rights per person. Each group has specific rights by default. A visitor can only read on the website, a member can edit documents and an owner can change the site structure. You should advise to limit the number of people in the owner group to deal with the structure and rights.
Some data should only be accessible by specific people because it deals with sensitive information. In this case, it may be necessary to create sub-sites with very specific, more restrictive rights. Indeed, it is preferable to manage sharing and access configurations via a specific SharePoint site library. This avoids the problems of rights with the creation of a sub-site, we subtract the inherited rights and we can manage more specifically the configurations, permissions.
This avoids the problems of inherited rights and complications in managing permissions. Be careful, however, not to multiply the number of subsites and once again complicate the management of permissions.
A good understanding of the risks is important for a better mastery and adoption of the tools. This is why it is important to communicate regularly on good practices, whether on OneDrive, Teams or SharePoint, in order to make users aware of security issues. But one of the challenges, especially to increase employee involvement, is to simplify the experience around data security.
There are tools such as Microsoft Purview Information Protection, which can be used to classify, encrypt sensitive information.
But to go further, each employee needs to have visibility to their own security and understand the consequences of an action achieved through its collaborative tools.
IDECSI offers a solution that meets this need, MyDataSecurity, where users can use a dashboard to monitor and validate who is accessing or who has permission to access their sensitive SharePoint library for example. The access review and remediation functions are particularly appreciated by our customers.
Recent articles
Subscribe to our newsletter and receive new contents every month
Our articles
These articles may
interest you