Security CheckUp: Simplifying risk review in M365
Lire l'article[NEW] MYDATAMANAGEMENT TO CLEAN UP YOUR OBSOLETE, UNUSED AND VOLUMINOUS DATA
Solutions
Effective response to six major challenges in data security
#1 user-interacting platform for detection
Discover the platform
Best practices to improve Microsoft Teams security
Download the infographicOur resources
Check out our useful resources for improving data protection
Microsoft 365
20 May 2022

With Microsoft 365 tools, the deployment of new services that users do not control increases the risk of data exposure.
According to a recent CESIN study, negligence or handling error by an internal administrator or an employee is one of the main causes of security incidents. (1)
Here are 4 use cases in Microsoft 365 collaboration tools to watch carefully to prevent illegitimate, unintentional or inappropriate sharing and avoid data compromise and leaks.
An important concept here is the data life cycle. The data life cycle is the process describing the circulation of data in an organization from its creation to its deletion.
One of the difficulties encountered by users in this collaborative context is the management of their data over time. Indeed, in a company that favors team collaboration, with exchanges and sharing, it is complex for users to know at all times where their data is, who has access to it and when their data should be reviewed or deleted.
This is all the more evident when it comes to one-off collaborations. Users give rights to their storage spaces (Teams team, SharePoint site or OneDrive folder) or share links and files externally. A review of rights is therefore essential to improve data governance and to control access.
Questions of confidentiality regarding data shared, particularly with external parties, may arise after the end of a collaboration.
We have the case of anonymous sharing in which users will transmit a link allowing access to a particular file to their contact partner. Often the person who is sharing anonymously will not protect the file with a password.
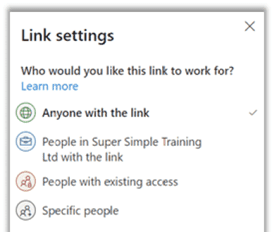
The problem which may then arise is the reduced level of security around the link’s distribution: there are no security rules on the identification of persons and no traceability on access.
The owner then no longer has control over their data: ‘Who has received my link?’, ‘Who has accessed my document?’ etc.
The management of individuals in private teams as well as in private channels is also important. A Teams team is intended to last over time, while a user can be involved in the project over a well-defined period. If a review is not carried out by the owner, that user will be able to continue to follow conversations and access files even months after a collaboration has ended.
This is also a problem in SharePoint or OneDrive. Rights can be applied at the level of document libraries or lower (files, folders) in case of inheritance breakage. The management of these rights will therefore be more complicated, as it will be necessary to go to the different levels of the directory to see and delete the rights granted.
Microsoft offers some solutions to manage rights over time: link expiration date for Anonymous sharing, and Azure AD Access Review.
But users have no centralized view or assistance to control and modify all their access, rights and sharing. As we can see, access review is a limitation of Teams, SharePoint and OneDrive.
Learn more about SharePoint security and the risks of over-sharing.
Delve is a very powerful search engine in the Office 365 suite. It pushes information of interest to users: files, messages, people.
Thanks to its ergonomic interface, users can quickly access the information they are looking for from the search bar.
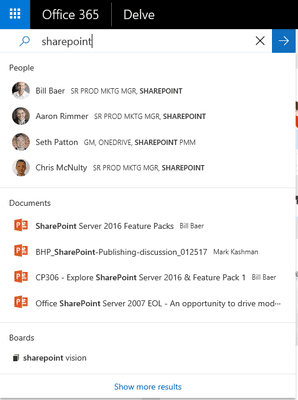
The DELVE search tool indexes the various documents shared intentionally or unintentionally. For example, if a sharing is set to ‘Organization-wide Link’ or ‘Anonymous’, its exposure to employees will increase. This can become dangerous, especially when sensitive or confidential data is involved.
On the surface, one might think that a ‘Link for the whole organization’ sharing is not really a risk, as only people who have the link can actually access it. Whereas with the Delve tool, the sharing is indexed and the file can become accessible from a search on a trivial query.
Once a document is indexed, it is then very difficult to determine who has accessed the information. The data may even be considered compromised, as it may pose integrity or compliance problems.
Microsoft Teams, a collaboration and meeting solution, has been rapidly adopted by users. Remote meetings and chat conversations are increasingly available to facilitate communication. However, if the tool is not well mastered, the management of exchanges can be complex.
Chat conversations do not provide a full guarantee of who can access the information.
Indeed, it is impossible to delete a Teams conversation and the management of members is open to all.
Find all the Microsoft 365 security best practices.
Today, therefore, access is virtually permanent. The example of ad hoc invitations to meetings is significant.
When I create a recurring Microsoft Teams meeting, it is normal for participants to have permanent access to the chat to find the latest exchanges. However, if I invite an internal or external user to one of the meetings, they will still have permanent access to the linked conversation. If the organizer does not regularly review the participants, all the users, whether correctly invited or not, will be able to follow the chat exchanges and the files exchanged.
Managing sharing through Teams conversations can also be a problem. Indeed, the review of who is accessing what is not directly accessible in Teams, but from the owner’s OneDrive.
Because changing the sharing link is complex and often not understood, the user will not review the files that were shared in these conversations. The links to the files therefore remain present and accessible indefinitely.
Power Automate is a Microsoft tool for automating repetitive tasks or processes. This application connects to several data sources such as external services (e.g. social networks).
Today, Microsoft 365’s Power Automate allows you to create workflows for Outlook, SharePoint and OneDrive to share or automate the sending and sharing of files, email transfers, etc.
The use of automatic inbox rules is a technique known to hackers to exfiltrate emails from the account with forwarding rules, to delete compromised emails or to copy/paste information without the user’s knowledge.
In the same way, Microsoft Power Automate allows tasks to be automated and lateral movements to be implemented within the IS and between connected applications. Thus, this function is diverted from its traditional use, allowing cybercriminals and malicious persons to exfiltrate data and evade Data Loss Prevention (DLP) tools.
It is important to detect dangerous operations immediately and to distinguish between what is legitimate and what is not: a potentially malicious transfer rule, illegitimate access to confidential files, sharing between different user groups.
IDECSI increases detection capacity and reliability and reduces the risks inherent in collaborative tools thanks to its expert monitoring platform and preconfigured threat models.
Similarly, users can identify abnormal operations or actions of their tools. To do this, they must be given the right tools and the review of access and permissions must be simplified. Users can ensure that operations comply with the security policy and their practices and correct them if necessary.
IDECSI has developed a unique methodology for access review to help companies to:
Simplify the review of permissions and sharing with the IDECSI solution.
(1) CESIN “Barometer of company cyber-security” – 2021
Recent articles
Subscribe to our newsletter and receive new contents every month
Our articles
These articles may
interest you