Security CheckUp: Simplifying risk review in M365
Lire l'article[NEW] MYDATAMANAGEMENT TO CLEAN UP YOUR OBSOLETE, UNUSED AND VOLUMINOUS DATA
Solutions
Effective response to six major challenges in data security
#1 user-interacting platform for detection
Discover the platform
Best practices to improve Microsoft Teams security
Download the infographicOur resources
Check out our useful resources for improving data protection
Microsoft 365
01 December 2022

To strengthen and improve the security approach of the Microsoft 365 suite and its applications, security and administration teams must be able to identify the native capabilities as well as the limitations of the tools and features provided by the vendor.
Microsoft offers several levels of licenses with varying degrees of security and compliance features.
The highest level is the Microsoft 365 E5 license, which offers comprehensive coverage and advanced analytics and data visualization capabilities for compliance and security risk assessment.
For budgetary reasons, most companies reserve this level of license for a sensitive, VIP population (executive committee members, security administrator, etc.). Other intermediate license levels, such as the Microsoft 365 E3 license, are typically chosen for the remaining users.
Finally, for users with more limited usage needs, the Microsoft 365 E1 license may be sufficient in terms of protection (occasional use, just access to the email service).
Given the absolute priority of securing data and collaboration tools, especially on M365, it is necessary to establish an initial inventory of what these E3 and E5 licenses include, in order to consider completing or strengthening them with complementary solutions for Microsoft 365.
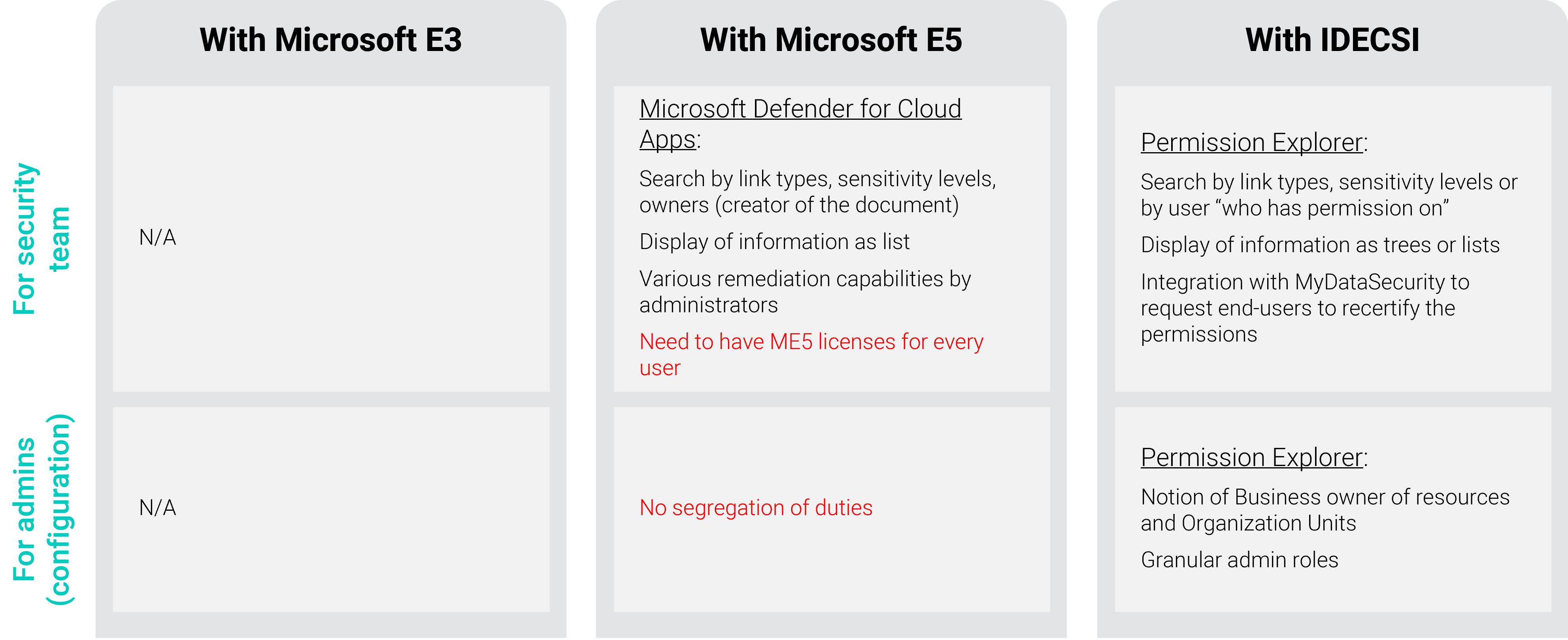
We have identified 3 use cases to focus on in order to detail and compare the native functions, Microsoft’s limitations and the IDECSI response :
The E3 license does not offer any control over permissions for administrators and users.
The E5 license includes Microsoft Defender for Cloud Apps (formerly MCAS).
Microsoft Defender allows you to:
However, there are some limitations:
All administrators will have the same level of information, it is not possible to set up a segregation of duties between entities. It is therefore necessary to appoint a central compliance team.
Note: investigation will only be possible only into internal users (except guests).
In addition to what Microsoft provides, IDECSI offers an analysis tool for administrators. It is possible to assign a granularity to the role of administrators according to their scope.
This tool, Permission Explorer, provides:
Integrated with the MyDataSecurity user platform, admin teams can ask users, via recertification campaigns, to validate permissions or access to their data.
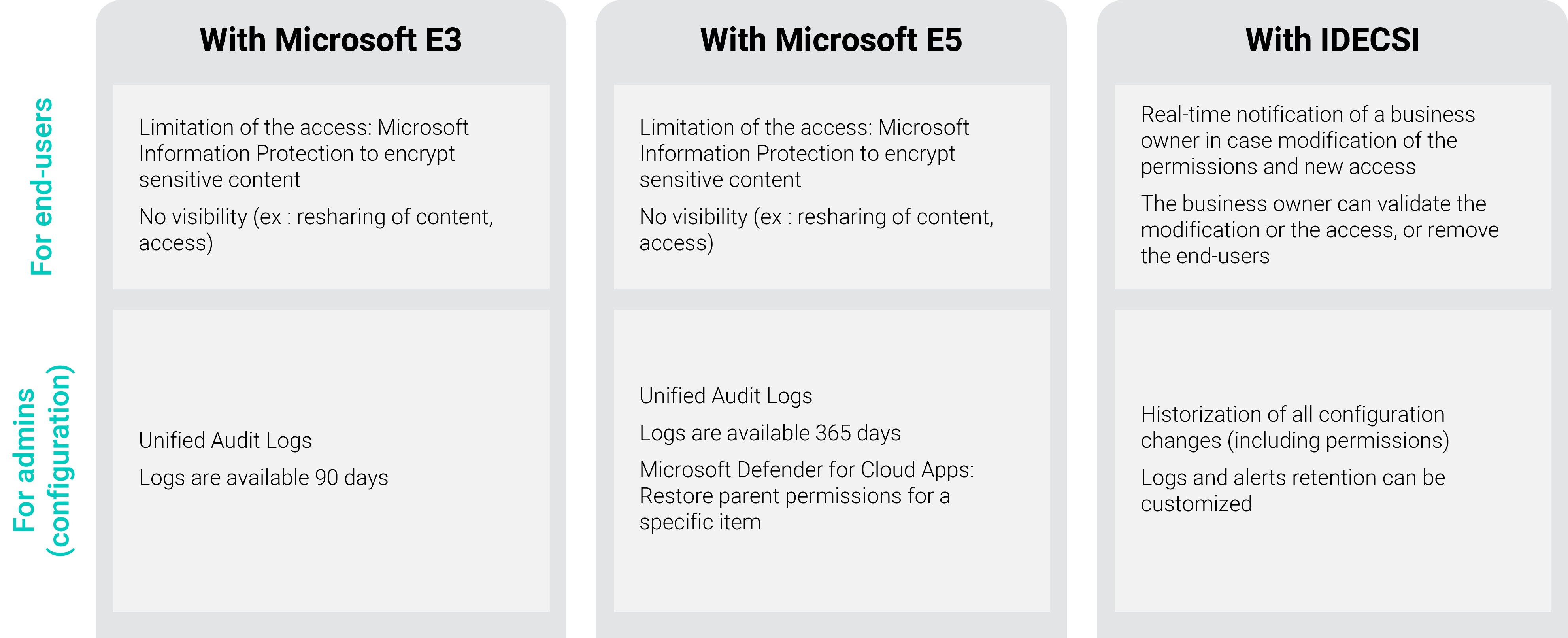
In Microsoft Purview, administrators can search the unified audit log to view user and administrator activity. These logs are available for 90 days.
They can do an audit manually to find out, for example:
Depending on the internal classification policy, users can encrypt sensitive content and restrict access with Purview Information Protection (MIP) labels.
With an E5 license, logs are available for one year (instead of 90 days on E3).
Administrators also have the Defender for Cloud Apps tool, which can restore permission inheritance (remove unique permissions and recover those of the parent folder or site).
Via Defender for Cloud Apps it is possible to set up a workflow to alert the owner of a document or a resource about deviating behavior (e.g. anonymous sharing).
Administrators can receive alerts when:
By default the user is not alerted but this can be programmed by workflows.
IDECSI leverages information from Microsoft Purview’s sensitivity tags to enhance the monitoring and protection of sensitive data.
Administrators can control sensitive data. They have a mapping of the data to sensitivity labels and their exposure.
They have access to the history of all configuration changes (including permissions) and log retention.
Alerts can be customized, to be aware of a policy change, a change in labeling actions, or sensitive shared data.
IDECSI also involves users and offers advanced monitoring with:
The review of access is an important step in data protection.
It involves ensuring that user access at the data level are consistent with an organization’s Microsoft 365 security policy and the user’s activity.
Read the article on the M365 collaboration tools access review
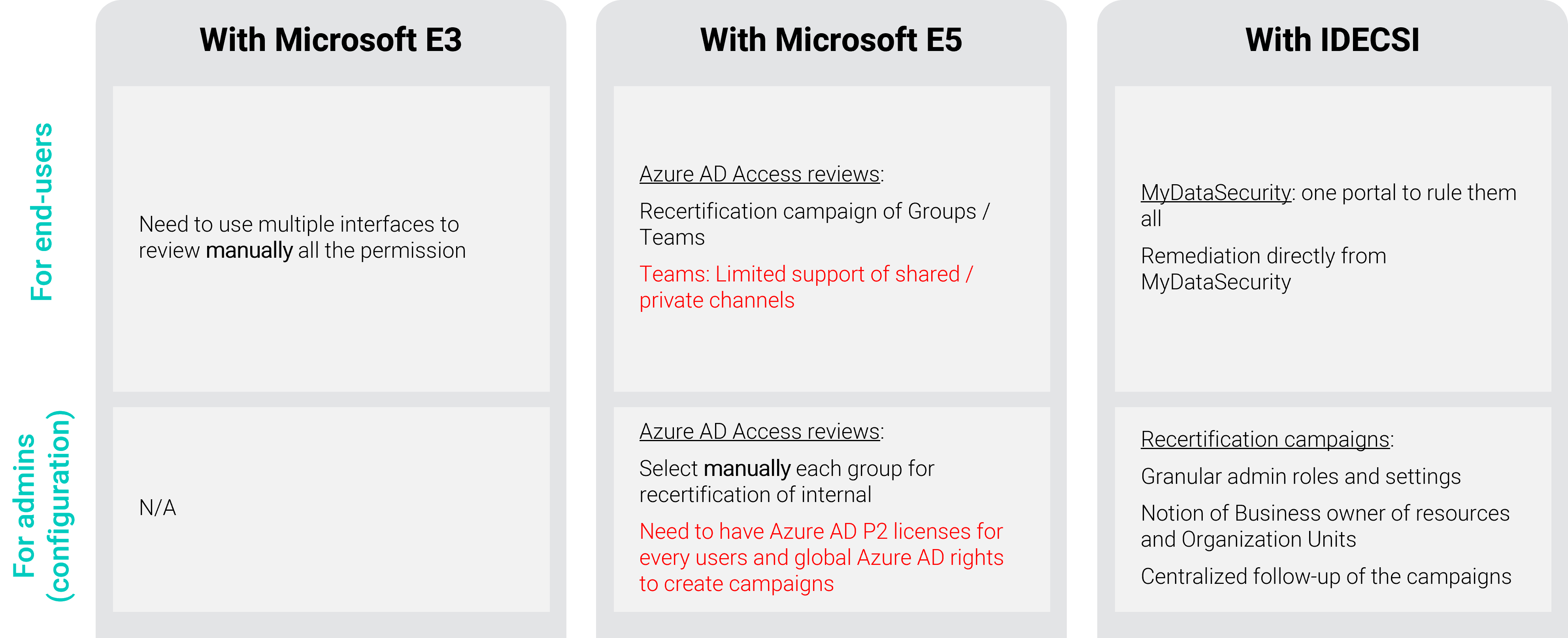
Administrators do not have a specific mechanism for launching overarching access review campaigns.
As for users, they can perform reviews but they will have to go to each application and manually remove, after several clicks, the permissions given on each file or group.
Via the Azure AD Access Reviews feature, offered in the Azure AD P2 license (included in E5), Azure AD administrators can manually track and recertify internal groups and run user campaigns.
Note:
- Only one license needed to review guests
- Review possible either on all groups including guests, or group by group (which requires to select them manually or by an API)
Recertification campaigns can be launched on Microsoft 365 groups: Teams or modern SharePoint.
The access review will apply to group members only. Permissions or sharing links made outside of a Teams team (on SharePoint for example) will not be part of the recertification campaign.
Azure AD Access Reviews allows users to be involved in access reviews.
Following the launch of the campaign, the owners of the Teams / SharePoint groups will receive an email with the group to be verified. The verification will only be carried out at the member level and will not affect shared channels.
Regarding the review of the permissions of other applications (OneDrive, Exchange for example), the approach will be the same as on the E3 license, i.e. manual through going on each one given permission.
IDECSI has developed a recertification tool, MyDataSecurity, which solves the constraints of volume and complexity in the access review process, allowing data security to be maintained over time.
Administrators have a platform to plan recertification campaigns. The setup is simplified to determine:
Reports on access review campaigns are available to track user validations and any troubleshooting initiated.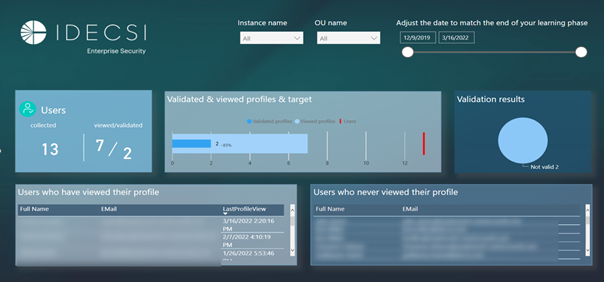
The user has a security dashboard to set up governance over his data and a review of access, sharing and configuration from a single portal, named MyDataSecurity.
In the context of a campaign, users will also receive a notification to recertify all permissions and will be able to apply automatic troubleshooting.
The Microsoft E5 license includes many security and compliance features and tools, but it represents a significant IT budget.
The IDECSI for M365 solution complements Microsoft’s security offering and increases the security of data both on-premises and on Microsoft 365. The platform offers 5 key features for a comprehensive data security approach: collection and traceability, user access review, admin control and audit, alerts and investigation, and consolidated reports.
Microsoft and IDECSI teams have been working on a mapping of the key security features of Microsoft 365. This document gives companies a better overview of the construction of a global and optimized system.
Recent articles
Subscribe to our newsletter and receive new contents every month
Our articles
These articles may
interest you